Author: Yambilla (contributed by Joy Blankson-Hemans)
Risk refers to any danger or threat, seen or unforeseen, which could negatively affect the socio-economic life of people. As countries globalize, they become exposed to various forms of risks – geopolitical, economic, physical or biological.

Threats to individuals and businesses include:
Hacking
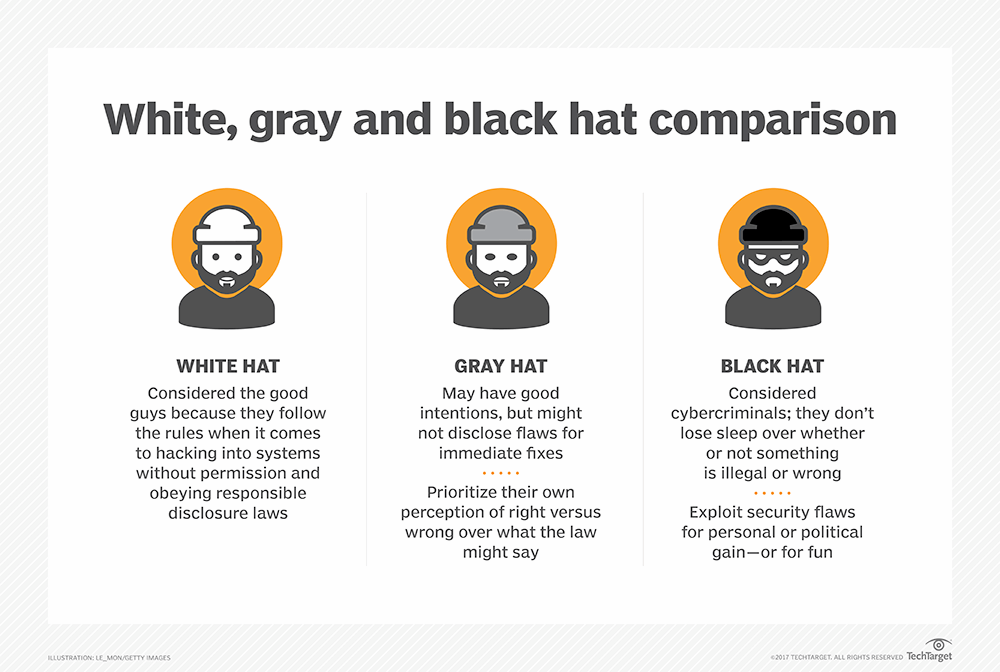
Hacking can be defined as unauthorized access to a computer, network or system. There are many types of hackers but the two most recognizable types are:
Black hat hackers are notorious for creating malware to infiltrate systems and are usually motivated by personal and financial gain. They can be amateur or highly experienced and will do anything from spreading malware to stealing personal details. Upon access, black hat hackers can either steal, manipulate victims and/or destroy the compromised system.
White hat hackers are “ethical hackers” that may be employed by companies and/or governments as security specialists looking for vulnerabilities. The key difference between white and black hat hackers is the presence of explicit legal permission to “infiltrate” by the system’s owner. Ethical hacking is considered an academic field and is taught through courses and training as well as conferences. One can even become a certified ethical hacker.
Hackers use various techniques to breach systems. For example, password cracking is a process of recovering passwords from data stored by a computer system. Other techniques include phishing, key logging and viruses. However, most systems now have measures in place to survive such attacks.
Examples of hacking:
- In 1999, a 15-year-old teenager, Jonathan James penetrated the computers of a US Department of Defense and installed a ‘backdoor’ on its servers which allowed him to intercept thousands of internal emails from different government organizations, including ones containing usernames and passwords for various military computers. He used the information to steal NASA’s software, which controlled the temperature and humidity of the International Space Station, thus causing the system to shut down for three weeks. He was caught and charged but later committed suicide when accused of collaborating with other hackers to steal credit card information.
- In 2009, Google China was attacked and the private information of millions of Gmail users in the US, China and Europe was compromised. This led Google to relocate its servers from China to Hong Kong, as it suspected the Chinese Government of the crime.
- In April 2011, Sony’s PlayStation Network was hacked and information containing personal data, including banking information of 77 million users was hacked.
- In 2018, the privacy of 500 million customers of Marriott Hotels was compromised – payment information, names, mailing addresses, phone numbers, email addresses, passport numbers, and even details of the Starwood Preferred Guest (SPG) account, a high-end card recently launched by the American Express credit card issuer for regular travellers.
- In 2021, a cyber-criminal gang calling itself DarkSide, took a major US fuel pipeline offline, demanding a ransom of up to 2 million dollars or more from Colonial Pipeline. Colonial hack: How did cyber-attackers shut off the pipeline?. A few days later, Colonial pipeline reportedly paid Darkside a sum of about $ 5 million before it returned online. (US fuel pipeline ‘paid hackers $5m in ransom’)
- Other attacks include: Travelex being held for ransom by hackers

All in all, these techniques result in significant consequences like identity theft, security breaches and other computer-related crimes.
Identity theft:
Identity theft is the deliberate and illegal use of someone’s information and identity in order to economically gain, obtain benefits, commit cyber crimes or even intentionally cause a loss to the victim.
Examples: In 2001, Abraham Abdallah tricked many credit card companies into providing him with information and used the identities of some of America’s richest, including Warren Buffet and Steven Spielberg, to steal millions of dollars. Read about his case here:
Cybercrime: A crime in which a computer is the object of the crime or is used as a tool to commit an offence (e.g hacking, child pornography, money laundering). Examples of a cybercrime:
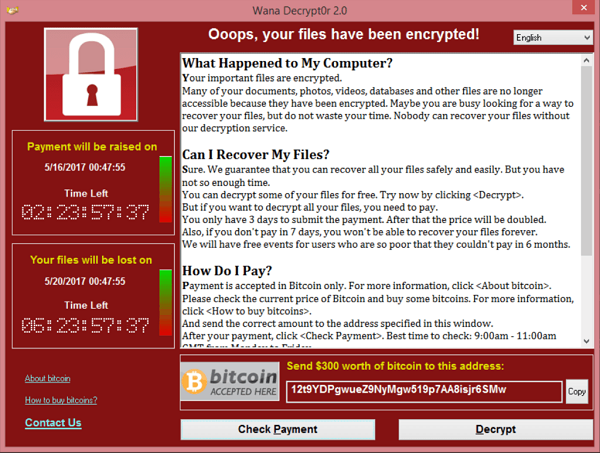
- May 2017 Wanna-cry ransomware attack: this was a worldwide “malicious software” that targeted computers running the Microsoft Windows operating system. The attack focused on encrypting the data of victims and demanding ransom payments in Bitcoin to safely gain back control. It affected more than 200,000 computers in 150 countries with damages exceeding several millions of dollars.
- A security breach occurs when a hacker successfully infiltrates a data source and extracts sensitive information from a private or confidential database. In 2016, UK, Tesco suffered a major security breach where cyber-criminals infiltrated the company’s banking system and stole money from 20,000 bank accounts.
- An example of a security breach is WikiLeaks, founded by Julian Assange. It operates as a not-for-profit organization that publishes secret information, news leaks and other forms of sensitive information for media organisations and the general public.

WikiLeaks has recently faced a lot of controversies involving interference with some government activities and has been accused of manipulating the information available to the public through leaks. In 2016, WikiLeaks published a searchable archive of more than 30,000 Hillary Clinton emails that have been released by the State Department. This created a negative press and distrust of Clinton’s professional capabilities and some critics cite this as one of the factors that led to her failed attempt at the 2016 presidency.
The implications of surveillance for personal freedoms
Reducing cybercrime has become a priority for businesses and law enforcement agencies, as the internet has become central to the development of modern society. As new technologies increase, their boundaries also increase and just as a method of protection has been established to handle particular risks an even bigger risk is birthed from these expanding boundaries.
In response to cyber-crimes such as hacking and identity theft, there has been a rise in surveillance and monitoring of individuals, which has been met with both praise and criticism.
Some critics argue that just because technology has paved the way to monitor the activities of internet users or individuals, in general, does not mean it should be used. China has endorsed the opposing view with the adoption of a rigorous mass surveillance system and is now consistently ranked as one of the worst abusers of internet freedom.
In November 2018, Chinese authorities published a law that requires applications like Alibaba and Tencent to keep a log of personal information on their users (including blog and chat room posts) and be readily available to provide this information and the names of registered users to the government if necessary. This is seen as a direct infringement on personal freedom.
Research: Find out other examples of infringements on the personal freedom of individuals in a given country.
Benefits of a surveillance society:
- CCTV cameras can improve safety and reduce crime, especially at night when people are most vulnerable.
- With the internet as a primary and central means of communication, terrorist groups like ISIS have used it as a medium to publish gory videos of the beheading of their victims. Hence, surveillance by law enforcement can be advantageous for regulating the content of the internet and protecting users.
- Surveillance can help ‘catch’ criminals. For example, it only took the FBI three days to release photos of the suspects in the Boston Marathon bombing.
- It can help improve urban facilities. Live cameras can be used to arrest speeding motorists, and traffic surveillance allows users to estimate the travel time to their destinations.
Dangers of a surveillance society
- Mass surveillance is expensive and requires a lot of hardware to set up the entire system.
- Surveillance can easily be abused and used to blackmail or coerce people. The power of surveillance was brought to light by the 2014 Sony Pictures Hack. Hackers, who were allegedly employed by North Korean authorities, stole personal information from Sony employees and threatened to carry out a terrorist attack akin to 9/11 if the controversial film, “The Interview”, was not pulled from theatres. The ability of surveillance to hold the sensitive personal information of users makes it a dangerous tool.
- Surveillance infringes on personal freedom. On a national scale, in January 2011, Ethiopian authorities filtered pictures of conflict and eventually cut off internet service to stop a revolt from spreading. This is an example of how personal freedom (e.g freedom of expression) can be compromised by surveillance of internet activities by the government.
Political, economic and physical risks to global supply chain flows
The more extensive a supply chain, the greater the possibility of its exposure to local threats and risks. This can be political, economic, social and physical risks for TNCs – the main architects of globalization.
Supply chain is defined as a “network between a company and its suppliers to produce and distribute a specific product to the final buyer. This network includes different activities, people, entities, information, and resources.”(Investopedia).
It includes various processes involved in getting a product from the producer to the consumer. For example, a Toyota saloon car has over 200 different suppliers, representing companies, individuals, producers, vendors, warehouses, transportation companies, distribution centres, and retailers.
The diagram below gives a general overview of the risks in the global supply chain:
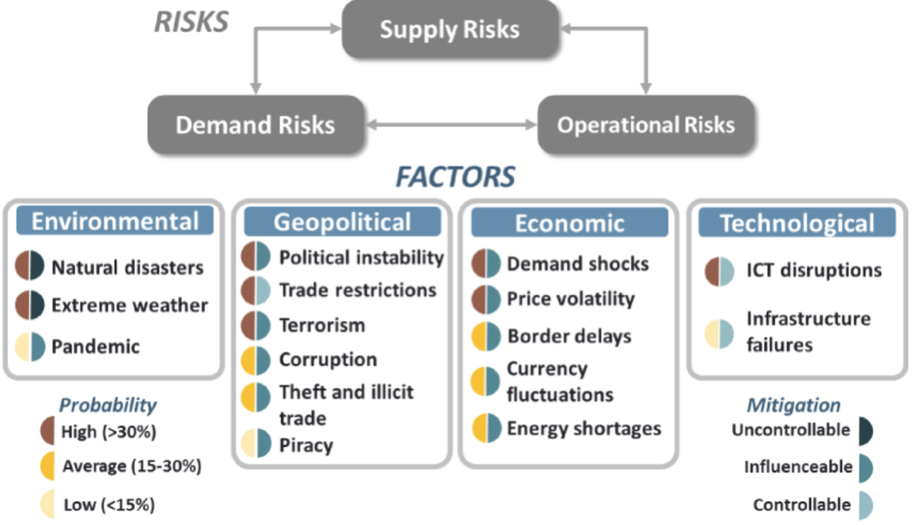
Examples of risks:
Political risks
- Political demonstrations – e.g. Foxconn iPhone components production in Vietnam was suspended following political demonstrations in the country
- Government sanctions – e.g US and EU oil companies halted operations in Russia following sanctions against the annexation of Crimea in 2014
- Rise in terrorist attacks – e.g. Daesh terror attacks that target holidaymakers in Tunisia led to TNC supply shocks for most tourist TNCs especially, hotels, restaurants and airline companies and decreased tourist revenue.
- Brexit is also a risk that is impacting heavily on the global supply chains of major companies. For example, the Honda Car manufacturing company has a plant in the UK. However, as a result of the uncertainties associated with the UK’s exit from the EU, the company has moved its production functions due to the implications this may have on its business.
Physical risks
- The Ebola outbreak in West Africa in 2016 seriously affected the supply chains of most companies depending on raw materials such as diamonds, cocoa, gold and other agricultural produce they obtain from the affected countries.
- The Coronavirus pandemic also affected the supply of raw materials for many companies in different parts of the world.
- The Tsunami that hit Japan in 2011 also impacted the supply of electronic spare parts as well as car engines such as Toyota, Honda etc, as these are mostly originating from the affected prefecture in Japan.
- Flooding in Bangladesh disrupted the supply of cotton for clothing manufacturing companies in many parts of the world.
Economic risks
- Economic downturns in different parts of the world can affect the supply of component parts for some manufacturers. This could be due to the collapse of businesses of subcontractors in the affected area or an increase in the price of raw materials, causing manufacturers to reconsider their reliance on such materials.
- Trade restrictions/wars such as the US-China trade war can cause substantial risks for businesses as there are uncertainties associated with such wars. It may also lead to a high cost of supplies of raw materials in the case of high tariffs on imported raw materials.
- Exchange rate fluctuations also create a lot of risks for businesses, especially in developing countries, where the local currencies frequently depreciate against the dollar. This could impact foreign investors relying on the import of raw materials from developed countries.
- Top 10 global supply chain risks
- Global Supply Chain Intelligence report reveals top supply chain risks in 2016
Case Study:
Supply Chain Disruption: This document contains three case studies. You may choose to specialize in one or two.
New and emerging threats to the political and economic sovereignty of states:
Political sovereignty is the complete and absolute freedom of any country to govern itself or manage its own affairs, without interference from another country. Ideally, every country is a sovereign state, however, membership in multi-governmental organizations such as the EU or UN can limit a country’s sovereignty.
Economic sovereignty, on the other hand, is the economic independence a country enjoys without any interference from another country – that is, by trying to influence market forces in the country. For example, the Francophone countries in West Africa ( Togo, Burkina Faso, Ivory Coast, Senegal etc) do not have full economic sovereignty, as the value of their currency is fixed by the Central Bank in France.
Increasing globalization is often associated with the loss of political and economic sovereignty of most globalized nations. This is partly responsible for the growth of nationalism in most advanced countries such as the USA, UK, Germany and France. The rising threats posed by increasing international migration and the economic challenges resulting from the relocation of manufacturing industries to emerging markets such as China, among many other factors have contributed to the loss of sovereignty of some globalized countries. This issue is covered in much detail under Local responses to global interactions.
Some examples of loss of political and economic sovereignty:
- The sale of part of the UK’s iron/steel industry at Sheffield to the Indian Company, Tata, is viewed by some critics of globalization as the ‘sale’ of the UK’s economic sovereignty to India.
- Many countries have lost their political sovereignty at one point or the other through invasions or military interference or war. For example, the invasion of Kuwait by Iraq on 2nd August 1990 led to several months of occupation of the country, until a UN mandate deemed it illegal. This led to the UN coalition force expelling Iraq from Kuwait.
- Some British clubs such as Manchester City, Chelsea, and Leicester City are owned by foreign businessmen. This could also be considered a loss of economic sovereignty.
- Two major airports in the UK – Heathrow and Gatwick airports are owned by foreigners despite their strategic importance to the UK. Similarly, most ports in the UK, in places like Liverpool, are foreign-owned.
- The greatest threat to the sovereignty of these countries is that there are special arrangements to exempt such foreign companies from paying taxes to other UK governments. For more details on this subject click on the link below:
- Who owns Britain?
- 11 American companies that are no longer American
- Famous British Brand that is foreign-owned
Profit repatriation and tax avoidance by TNCs and wealthy individuals
TNCs and rich individuals play a key role by contributing to the economic development of countries through taxes they pay on their profits. For example, in 2012, Apple paid about $6 billion and Exxon Mobile paid $32 billion as corporate tax to the US government. The contribution made by these companies makes them ‘too significant’ for any government not to recognize their relevance. However, some TNCs and individuals have routed their wealth or profits from investments in some countries to tax havens such as Panama, Switzerland etc.

A recent report from the Institute on Taxation and Economic Policy has found that 366 of America’s largest 500 companies maintain 9,755 tax haven subsidiaries holding over $2.6 trillion in accumulated profits. Despite only having three tax haven subsidiaries in Ireland, Apple stashes the most cash offshore by far, some $246 billion which helps the company avoid $76.7 billion in U.S. taxes (statista.com).
In some cases, foreign TNCs may repatriate their profits to their home country. Profit repatriation is the transfer of profits or capital from a foreign country to the home country of the foreign investor. This is a form of threat that affects the sovereignty of states in which the industries are located and undermines their capacity to effectively control TNCs due to fear of losing them to other countries. It also undermines their capacity to raise revenue to undertake socio-economic projects in the country. Profit repatriation, therefore, may constitute a threat to the economic and/or political sovereignty of states.
Similarly, TNCs practice tax avoidance by repatriating profits made in overseas countries to other countries with lower corporate tax rates, thereby threatening the economic sovereignty of their parent states. This may lead to a fall in the country’s GDP or reduce the country’s internal revenue needed for development. The International Monetary Fund (IMF) estimated in July 2015 that profit shifting by multinational companies costs developing countries around US$213 billion a year, almost two per cent of their national income. Transfer pricing as tax avoidance
Examples of profit repatriation and/or transfer pricing include:
- Car manufacturing companies in Europe (BMW, Mercedes and Volvo) and the USA (Ford, Tesla) have opened branches in China to take advantage of low corporate taxes and the large market size. This is known as corporate migration.
- Banks and other financial institutions have also relocated their offices to some EU countries like Luxembourg, Switzerland and Ireland etc. which offer a lower corporate tax. Tax havens in the world. Goldman Sachs Group has the most tax havens of any large U.S. company by far with 905 in total, including 511 in the Cayman Islands (though the company does not have an office there), 183 in Luxembourg, 52 in Ireland and 41 in Mauritius. Morgan Stanley is in second place with 619 tax haven subsidiaries, while ThermoFisher Scientific rounds off the top three with 199 (Statista.com). Even though small island nations like Bermuda and the Cayman Islands are notorious for tax avoidance schemes, the Netherlands is actually the country most frequently used as a tax haven by American companies.
- Some TNCs may also hide their profits in tax havens rather than transferring them to their home country. An example of such tax havens is Panama, the Cayman Islands, Switzerland and Monaco. It is estimated that at least $270 billion is “invested” by Canadian companies in tax havens like Barbados, Luxembourg, the Cayman Islands, the Bahamas and Bermuda.

- Individuals may also hide their wealth in such tax havens. The Panama papers published by a global consortium of investigative journalists in 2015 revealed that a law firm, Mossack Fonseca, based in Panama acted as a haven for over 300,000 companies and individuals in the world. The release of the papers showed that wealthy individuals are secretly hiding their wealth in tax havens. China’s rich rush to shelter $1 trillion from new taxes
- Countries may lose their economic sovereignty through the sale of assets to other countries. Many developing countries have sold their corporations to foreign countries in the hope that they would efficiently manage these corporations. For example, China has invested about 800 million Pounds in the Manchester City airport project and owns 10% shares in Heathrow airport. Vodafone owns about 70% of Ghana Telecom, as well as many other such investments in other African countries like Egypt.
- Another publication that revealed where the secret wealth of world leaders was exposed in October 2021 is the Pandora Papers. Watch the YouTube video for details.
Disruptive technological innovations
Disruptive technology is any technology that displaces an existing one, resulting in a complete restructuring of the industry. Examples of disruptive technology include:
- Personal computers replacing the type-writer, transforming the way we communicate
- Email replacing letter-writing, thus eliminating the need for a postal address and transforming communication
- Mobile phones replacing landlines, transforming the communication
- The internet, disrupting television, mobile phone calls, etc
Examples of destructive technology:
Drones

A drone is an unmanned aerial vehicle (UAV) that is controlled by a person on the ground or remotely by a computer.
Advantages of drones:
- They can be used for military combat, reducing the need for boots on the ground
- They can be used in agriculture for spraying herbicides and controlling pests
- Drones can be used for the delivery of medical supplies – recently introduced in Ghana
- In Canada, drones are used for courier services; delivering supplies to remote areas
- it can be used for wildlife conservation – for controlling the movement of animals in the forest and remote areas
- Drones can be used in photography – to take aerial photographs
- it can be used to study weather phenomena – it can enter the eye of a storm (hurricane) to measure its characteristics.
Disadvantages of drones:
- Drones can malfunction due to human or computer errors, causing damage to life and property
- Drones can very expensive to purchase and maintain.
- Drones for military purposes can cause the accidental death of innocent people
- Drones can invade a person’s privacy, in the case of drones with infrared sensors and powerful cameras
- Drones can disrupt air transport, as happened at Gatwick airport in the UK in December 2018, causing disruption to several flights
3D printing
3Dprinting or additive manufacturing is a process of making three-dimensional solid objects from a digital file. The creation of a 3D printed object is achieved using additive processes that enable you to produce complex (functional) shapes using less material than traditional manufacturing methods (3D Printing.com)

The usefulness of 3D Printing;
- It can be used to print prosthetic parts for humans and even animals.
- It can be used for the construction of houses, quickly and economically
- It is useful for printing musical instruments
- Possibly for printing houses on Mars
- It is used for printing parts of aeroplanes such as fuel nozzles and jet-engines
Use the links below and list 7 advantages and 4 disadvantages of 3D printing and watch as many videos as you can on 3D printing
Disadvantages of 3D Printing:
Research assignment:
- In what ways has 3D disrupted modern technologies?
- What are the implications of 3D printing for states and individuals?
- See 10 disadvantages of 3D printing
The correlation between increased globalization and renewed nationalism/tribalization
In response to increasing global interactions individuals, civil society organizations and sometimes entire states have started opposing the free movement of goods, people, ideas and capital. This is particularly true in countries that have lost more to globalization such as the UK, and the USA. EU and some developing countries. The rise of populism, tribalism, racism and anti-immigration/globalization in these countries suggest that the loser of globalization are beginning to show their concerns through these movements.
Examples of anti-globalization movements:
- Donald Trump
- Marine le Penn
- UKIP Nigel Farage
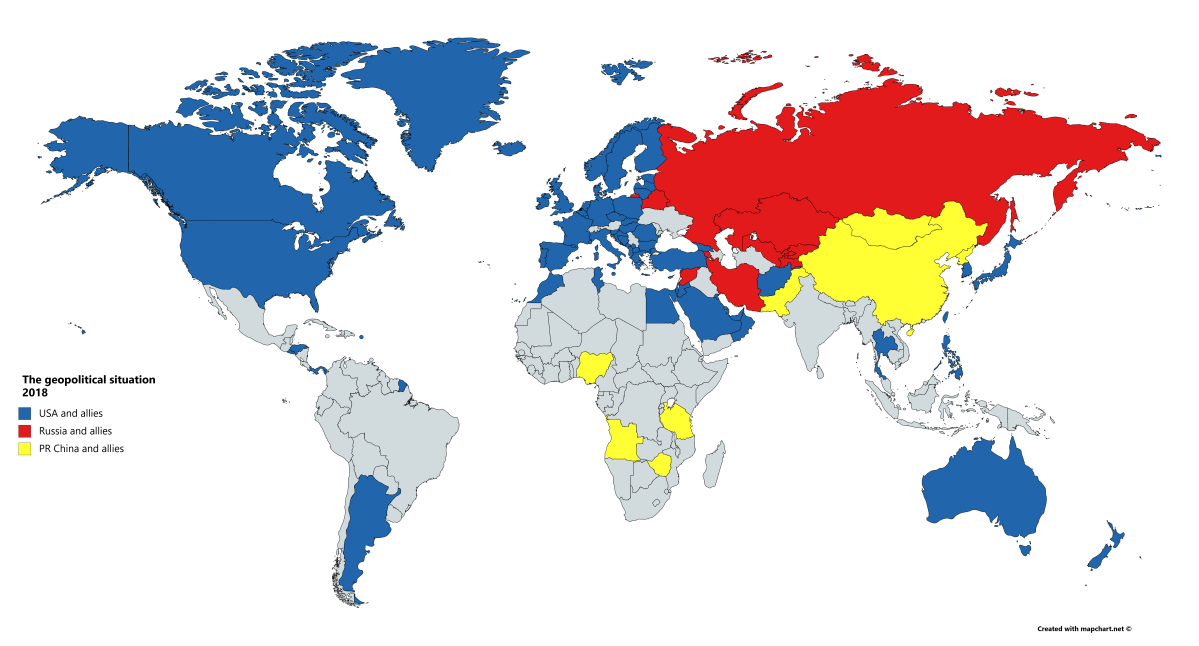
Two detailed examples to illustrate geopolitical tension/conflict
5 replies on “Geopolitical and economic risks”
Very good post! We are linking to this particularly great content on our site. Keep up the good writing.
LikeLike
Spot on with this write-up, I absolutely believe that this website needs a great deal more attention. I’ll probably be back again to read more, thanks for the information!|
LikeLike
I wanted to thank you for this fantastic read!! I absolutely enjoyed every little bit of it. I have you saved as a favorite to look at new stuff you post…|
LikeLike
This is my first time paying a quick visit here and i am genuinely pleased to read everything at one place.|
LikeLike
Hey there! I just would like to offer you a big thumbs up for your excellent information you’ve got here on this post. I will be coming back to your website for more soon.|
LikeLike